Activities
1. Start with an architectural draft
In this component, it is essential to define and align the overall system architecture for your data-driven use case. [1][2] This involves identifying the different technical components involved, how they interact, and what authorisations, adjustments, or interfaces may be needed within existing infrastructure.[1]
The goal is to ensure that your architecture supports data collection, storage, processing, analysis, and visualisation, while complying with legal, operational, and cybersecurity requirements. [1][3][4]
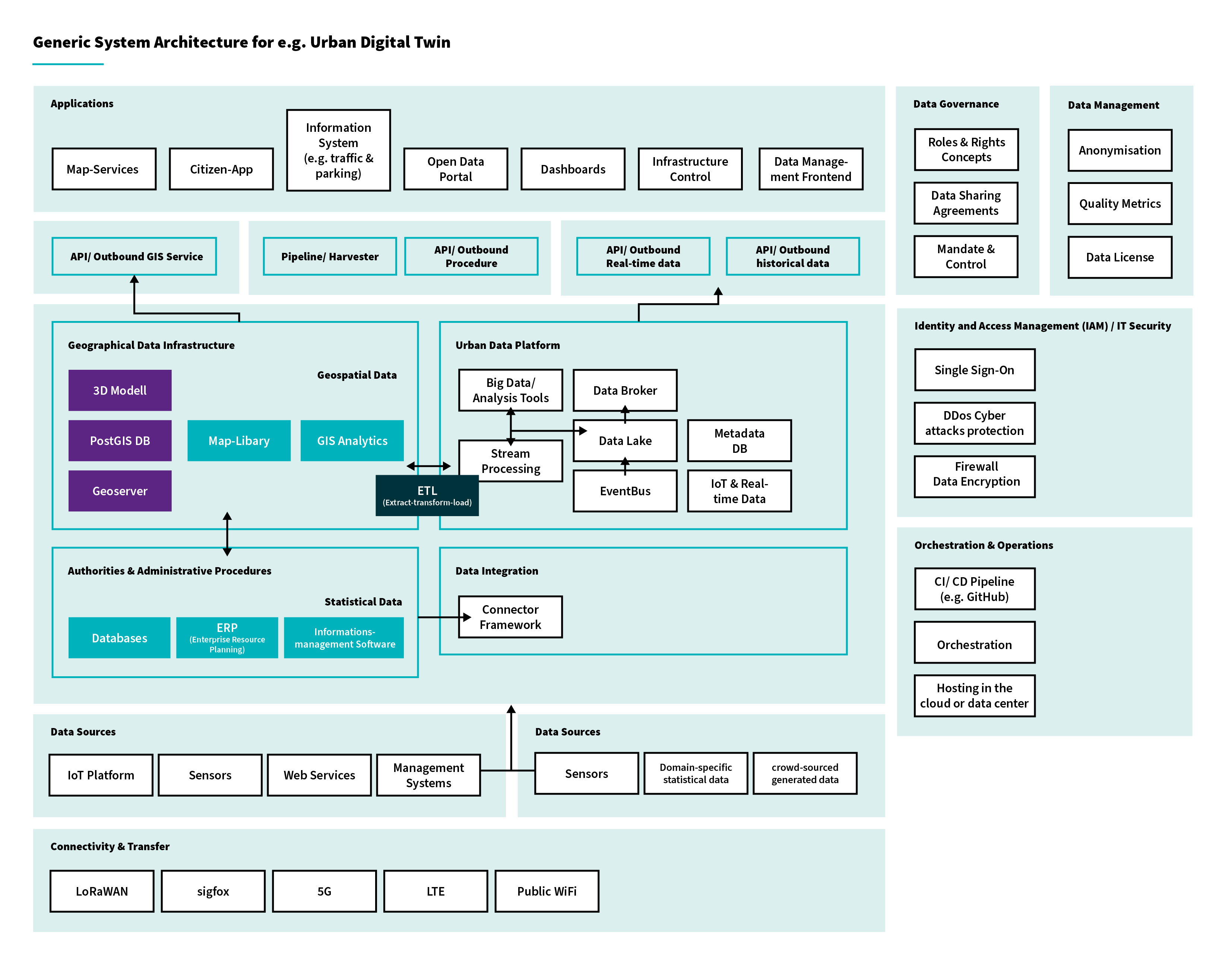
Components to consider in the architecture:
- GDI: Define how your architecture will integrate with the municipal or national GDI. [5][6]
- UDP: Assess how your use case connects to the existing Urban Data Platform.
- Did you identify all the data pipelines, APIs, and connectors?[7]
- Compatibility with metadata catalogues?[8][9]
- Applications: ensuring the connection of dashboards, mobile apps, public portals, internal tools to the backend. [1]
2. Select technology
Once you have a clearer picture of your required system architecture, you can start selecting the platforms, tools, and frameworks that are still missing (e.g. cloud services, AI tools, GIS mapping software, etc.). [7]
At this stage, it’s crucial to evaluate each new tool or platform carefully:
- How interoperable is it with your existing systems?[7][8]
- Who holds data sovereignty?
- What is the maintenance and support model?[10][11]
- What are the costs for implementation, long-term service and upkeep?
Keep in mind that even Open Source tools can lead to high maintenance costs if these aspects are not clearly understood and planned from the beginning.
3. Ensure data integration
If you’re starting know the data integration, you have made sure that your data complies with legal and privacy regulations. Your data is if necessary anonymised, pseudonymised and aggregated. [12] Your datasets are standardised and include complete metadata (e.g. source, update frequency, licensing, schema). They have harmonised formats (e.g. time formats, units, geospatial references), which is crucial to ensure consistent coordinate systems and spatial granularity.[5][13]
This solution offers a practical, ready-to-use framework that helps municipalities turn scattered, underused data into a well-governed, interoperable, and innovation-driving asset, making it a must-see for anyone working in public-sector digital transformation.
Semantic interoperability is especially important when merging datasets from different municipal departments or external partners.[8][9]
You’ve also clarified the ownership and usage rights of your data. Typically, you’ll be working with open data, shared data, or shared analysis results. Data intermediaries and intermediation services can support you in preparing or acquiring the needed datasets.[14] [10][15]
As part of integration, resolve any open questions related to cloud services and cybersecurity. Depending on your use case, you may have specific requirements for storage capacity, especially for live data. Decide early on what kind of data archiving system and concept you need to store, access, and evaluate collected data.[16][17]
This solution introduces a practical metadata schema that tackles the toughest technical, organisational, ethical, and regulatory barriers to smart-city interoperability, making it an essential resource for anyone trying to seamlessly connect heterogeneous data sources.
In this phase, open APIs are essential for integrating data from different systems. You should integrate not only real-time data (e.g. from your own scanners), but also historicised data, which can be valuable for forecasts and analysis.[18]
ETL pipelines (Extract, Transform, Load) help you manage how data flows into your platform. Consider tools and existing workflows to automate this process including error handling and logging. [19]
4. Develop a MVP (Minimum Viable Product)
During the development you will dive in the data integration and will have to tackle various problems. It is therefore important to also imagine the simplest version of the product that you want and need to build to answer your initial problem. For your MVP you can prioritise to integrate only the minimum necessary data so you can ensure that the solution brings value.
Early feedback from users may reveal that some datasets are unnecessary or that additional ones are needed. [22][23]
With the MVP you can also control or clarify your data governance roles and responsibilities. Is the maintaining of integrated data, updating pipelines, and addressing of data errors functioning?
5. Create a user interface
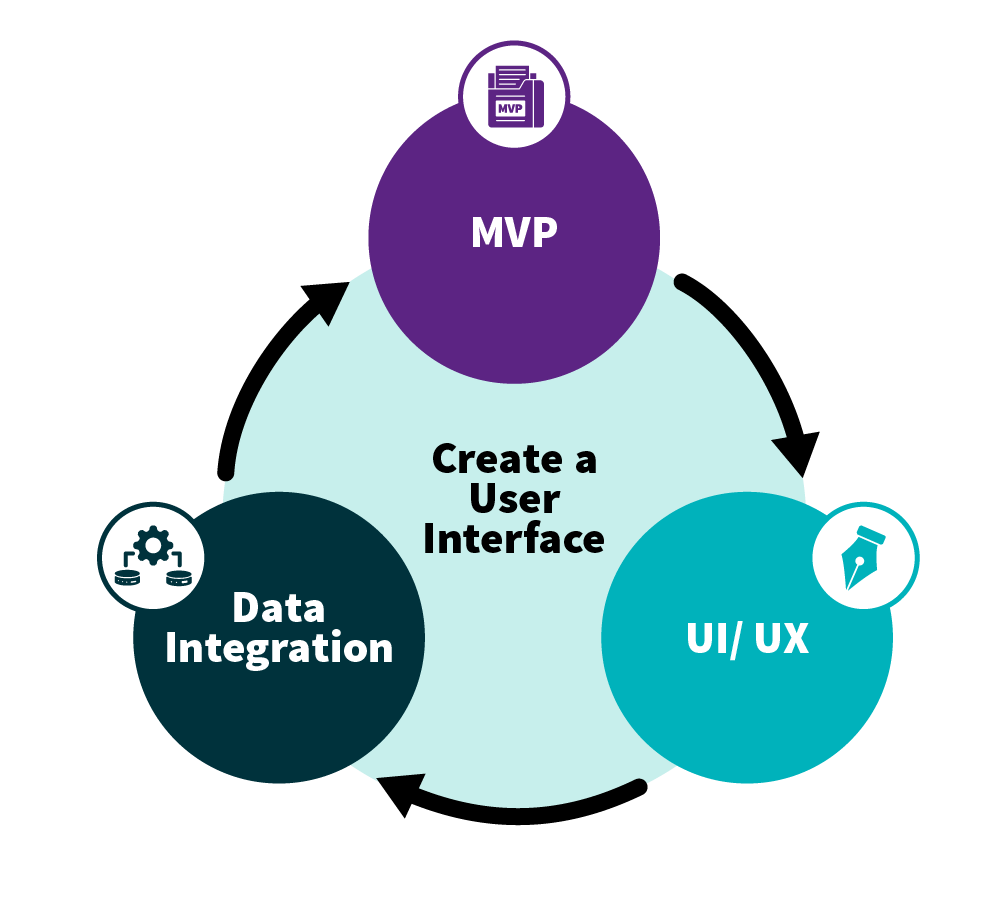
It is important to have a user interface which embrace the corporate design from your organisation, as such it is easier for all employees and eventually citizen to identify themselves with the new tool and to use the interface.
For those responsible of the data integration it is crucial to know in advance how the integrated data will be visually displaced (type of dashboards, graphs, maps…) in order to structure it accordingly during the integration.
Since it’s an MVP, some data will be missing, delayed or still be incorrect. For the user experience it is important to plan what the user interface (your system) will display if it’s the case. [24]
MVP, UI/UX and Data Integration are a connected trio and it is therefore important to see them as an iterative loop.[22][23][24]
6. Check for cybersecurity & do a general testing of the MVP
It is now time to test with real users your MVP! It will help you to adjust data flows and visual elements accordingly. The feedback loops will also help to validate whether the data integration meets the expectations and needs of the first users.
You may also focus at this point on intuitive use of your solution: not just for data experts, but for non-technical users (e.g. municipal employees, citizens), your final target group. This maybe the good time to start preparing guides and info sessions.
Verify again compliance with data protection, cybersecurity, and public sector IT regulations. Your MVP after the feedback loop may differ from your original planning.
Here are some key thoughts on cybersecurity aspects during and after the MVP testing:
- Document how you comply with cybersecurity policies. This may be required for audits or future expansion.
- Use secure protocols for the data transfers from APIs, databases, sensors etc.
- APIs endpoints are protected against unauthorised access
- Access control and authentication, logging and monitoring are already in place for the MVP: you can track suspicious behaviour, alerts are sent when triggered by defined anomalies
- Ensure backup and recovery procedures mechanisms: what happens if there is a data loss?
- Vulnerability scanning and penetration testing: Perform automated vulnerability scans of your application and infrastructure.
Resources
1. D4A Best Practices
2. D4A Training Modules
3. "Go deeper" - Insights on a Method
- Design Thinking
4. Academic papers
In our D4A knowledge base you will find more on the topic of data openness, data management or data risks
Sources
[1] NIST (National Institute of Standards and Technology) (2022) SP 800-160 Volume 1 Revision 1: Engineering Trustworthy Secure Systems (publication webpage). Available at: https://csrc.nist.gov/pubs/sp/800/160/v1/r1/final
[2] NIST (National Institute of Standards and Technology) (2021) SP 800-160 Volume 2 Revision 1: Developing Cyber-Resilient Systems (publication webpage). Available at: https://csrc.nist.gov/pubs/sp/800/160/v2/r1/final
[3] ISO (International Organization for Standardization) (n.d.) ISO/IEC 27001:2022 — Information security management systems (standard overview webpage). Available at: https://www.iso.org/standard/27001
[4] European Union (2016) Regulation (EU) 2016/679 (General Data Protection Regulation — GDPR) (legal text). Available at: https://eur-lex.europa.eu/eli/reg/2016/679/oj/eng
[5] European Union (2007) Directive 2007/2/EC establishing an Infrastructure for Spatial Information in the European Community (INSPIRE) (legal text). Available at: https://eur-lex.europa.eu/eli/dir/2007/2/2024-11-26/eng
[6] GDI-DE (Geodateninfrastruktur Deutschland) (n.d.) Interoperability (INSPIRE technical implementation) (webpage). Available at: https://www.gdi-de.org/en/INSPIRE/technical%20implemantation/interoperability
[7] OGC (Open Geospatial Consortium) (n.d.) OGC Standards Overview (webpage). Available at: https://www.ogc.org/standards-overview/
[8] Publications Office of the European Union (n.d.) DCAT-AP for data portals in Europe (specification webpage). Available at: https://op.europa.eu/en/web/eu-vocabularies/dcat-ap
[9] Interoperable Europe / SEMIC (2024) DCAT-AP 3.0.0 release (specification webpage). Available at: https://semiceu.github.io/DCAT-AP/releases/3.0.0/
[10] European Union (2022) Regulation (EU) 2022/868 (Data Governance Act) (legal text). Available at: https://eur-lex.europa.eu/eli/reg/2022/868/oj/eng
[11] Gaia-X (n.d.) Policy Rules and Architecture of Standards (PRAAS) (PDF). Available at: https://sriw.de/fileadmin/sriw/files/gaiax/gaia-x-policy-rules-and-architecture-of-standards.pdf
[12] European Data Protection Board (EDPB) (2025) Guidelines 01/2025 on Pseudonymisation (webpage). Available at: https://www.edpb.europa.eu/our-work-tools/documents/public-consultations/2025/guidelines-012025-pseudonymisation_en
[13] ISO (International Organization for Standardization) (2019) ISO 19111:2019 — Geographic information — Referencing by coordinates (standard overview webpage). Available at: https://www.iso.org/standard/74039.html
[14] European Union (2019) Directive (EU) 2019/1024 on open data and the reuse of public-sector information (legal text). Available at: https://eur-lex.europa.eu/eli/dir/2019/1024/oj/eng
[15] European Commission (n.d.) EU register of data intermediation services (webpage). Available at: https://digital-strategy.ec.europa.eu/en/policies/data-intermediary-services
[16] ENISA (European Union Agency for Cybersecurity) (2013) Good Practice Guide for securely deploying Governmental Clouds (report PDF). Available at: https://www.enisa.europa.eu/sites/default/files/publications/Good%20Practice%20Guide%20for%20securely%20deploying%20Governmental%20Clouds.pdf
[17] NIST (National Institute of Standards and Technology) (2020) SP 800-53 Revision 5 Update 1: Security and Privacy Controls for Information Systems and Organizations (publication webpage). Available at: https://csrc.nist.gov/pubs/sp/800/53/r5/upd1/final
[18] ISO (International Organization for Standardization) (2025) ISO 14721:2025 — Reference model for an open archival information system (OAIS) (standard overview webpage). Available at: https://www.iso.org/standard/87471.html
[19] OpenAPI Initiative (n.d.) OpenAPI Specification (specification webpage). Available at: https://spec.openapis.org/oas/
[20] IBM (n.d.) What is ETL (extract, transform, load)? (webpage). Available at: https://www.ibm.com/think/topics/etl
[21] NIST (National Institute of Standards and Technology) (2006) SP 800-92: Guide to Computer Security Log Management (publication webpage). Available at: https://csrc.nist.gov/pubs/sp/800/92/final
[22] Ries, E. (2011) The Lean Startup: How Today’s Entrepreneurs Use Continuous Innovation to Create Radically Successful Businesses (book). Available at: https://books.google.com/books/about/The_Lean_Startup.html?id=tvfyz-4JILwC
[23] Schwaber, K. and Sutherland, J. (2020) The Scrum Guide (2020) (PDF). Available at: https://scrumguides.org/docs/scrumguide/v2020/2020-Scrum-Guide-US.pdf
[24] ISO (International Organization for Standardization) (2019) ISO 9241-210:2019 — Human-centred design for interactive systems (standard overview webpage). Available at: https://www.iso.org/standard/77520.html
Last accessed and edited 03.2026